Managed Services
Complete Visibility & Protection
You need cybersecurity, but should you be managing it, staffing it, or even owning it?
There is a great chance you can reduce your overall staffing and business costs while improving your cybersecurity posture by using a 3rd party managed service.
Are managed services right for you?
- Are budgets being reduced?
- Is training too expensive?
- Has cybersecurity become too complex?
- Are resources being re-focused and re-tasked?
If you answered “Yes” to two or more of these questions then A2N’s Managed Services might be right for you.
Don’t be forced into a “one size fits all” solution.
We have a wide variety of manufacturer and Cloud based solutions to select from and we fully customize your managed services for your unique needs and environment.
Are you expecting too much from your IT staff?
Your IT staff are expected to handle all types of issues, from end user applications to database configuration. They are often a jack-of-all-trades and experts in little. But, cybersecurity is complex and requires skilled and knowledgeable professionals to ensure it is done right. Use A2N managed services because one simple mistake can make the difference between maintaining your brand or making headlines.
Fully manned 7x24x365
Unlimited changes & support calls
Total & complete visibility
Our SLAs Offer Unparalleled Value with 7x24x365 SOC and Unlimited Services
| > 7x24x265 Monitoring | > 7x24x365 Alert & Response | > 7x24x365 Change Windows |
| > Unlimited Policy Changes | > 7x24x365 Support Calls | > Unlimited Support Calls |
| > Incident Investigation & Support | > Monthly Reports & Reviews | > Change Control Management |
Managed Firewall & WAF
Managed Firewall provides administration, monitoring, response, support and maintenance of firewall infrastructures; while freeing clients from the burden of policy management, upgrades, patch deployment and troubleshooting.
Having a firewall is a cybersecurity fundamental but these devices have become highly evolved; they are no longer simply Red Light/Green Light appliances, and play a key strategic role in protecting your perimeter, Cloud and internal networks. Utilizing Unified Threat Management, (UTM, including; URL, WebAV, AppControl, IPS, SSL Decryption, SDWAN) services that come with most firewalls is the intelligent play when protecting the enterprise but it can come with unexpected complexity and concerns.
Outsourcing this complexity to the highly certified exerts within our Managed Services Team will remove the uncertainty and restore the peace of mind you deserve, because we know you have other issues to contend with.
Managed WAF: WAF or Web Application Firewall is essentially, as the name suggests, a firewall for applications. It is highly specialized in the inspection of HTTP traffic for the sole purpose of protecting your web based applications and the servers they reside on.
A web application firewall (WAF) protects web applications from a variety of application layer attacks such as cross-site scripting (XSS), SQL injection, and cookie poisoning, among others. Attacks to apps are the leading cause of breaches – they are the gateway to your valuable data. With the right WAF in place, you can block the array of attacks that aim to exfiltrate that data by compromising your systems.
Did You Know…
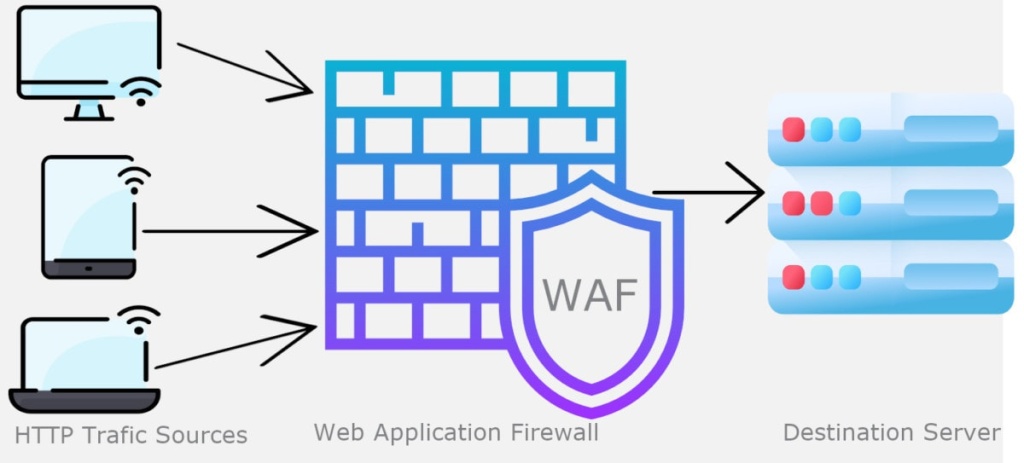
A WAF can do so much more than simply protect web applications from attack, they can also provide SSL Certificate Offloading , Load Balancing incoming HTTP/HTTPS traffic across multiple destination servers (called Application Redirection.) and some WAF can also participate in the Global redirection of traffic (traffic originating in North America will remain in North America).
Managed SD-WAN
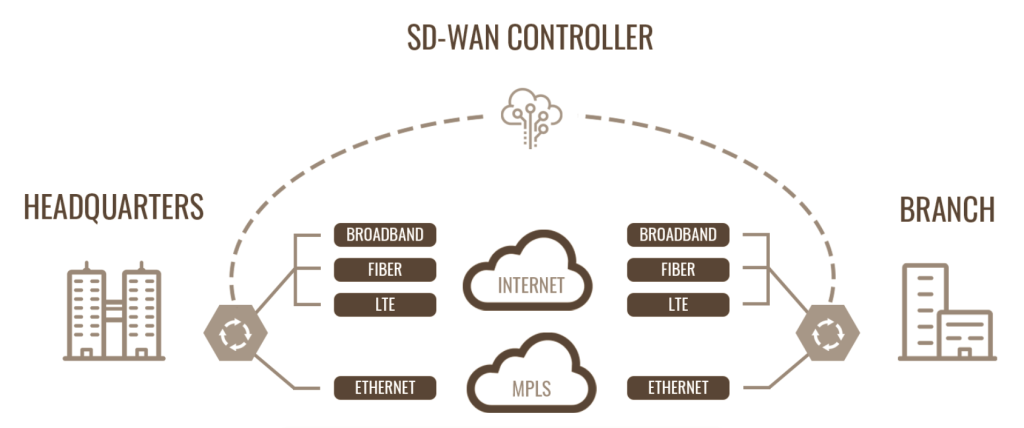
Managed SD-WAN is a game changer for many customers looking to improve connectivity between their HQ & remote offices while reducing dependency on slower and more expensive MPLS and moving to less expensive but faster Internet. In fact SD-WAN is one of the fastest growing markets in the cybersecurity industry and continues on that path for the foreseeable future.
SD-WAN uses inexpensive software technologies to control and manage the connection between multiple links which could include; Internet, MPLS, 4/5G and SIP Trunks. This software monitors the links for jitter, signal strength and load and regulates and balances the traffic for optimum use.
A2N uses top SD-WAN solutions like SilverPeak, Fortinet and Aruba SD-Branch. We can even incorporate SASE directly into SD-WAN depending on the solutions in use.
Managed SIEM & SOAR
Are you collecting logs but have no time to review them?
Are your IT staff professionally trained to correlate, analyze and interpret log data?
Do you conduct threat hunting using EDR, Indicator of Compromise and active Threat Intelligence?
SIEM (Security Information & Event Management) can be a difficult solution to manage because it uses so many different networking & security sources to correlate and interpret information against. Experienced IT Management understand the complexity of managing an in-house SIEM and often elect to outsource the service to a 3rd party to deploy faster, reduce setup and training costs and leverage the expertise of cybersecurity specialists.
A2N’s Managed SIEM is a defense-in-depth solution combining a breadth of technologies allowing for world class protection and threat hunting capabilities across your Enterprise. Our SOAR (Security Orchestration, Automation and Response) capability allows for instant policy change and protection when threats are identified.
All SIEM Solutions are Managed 7x24x365 by our Fully Staffed Operations Centre
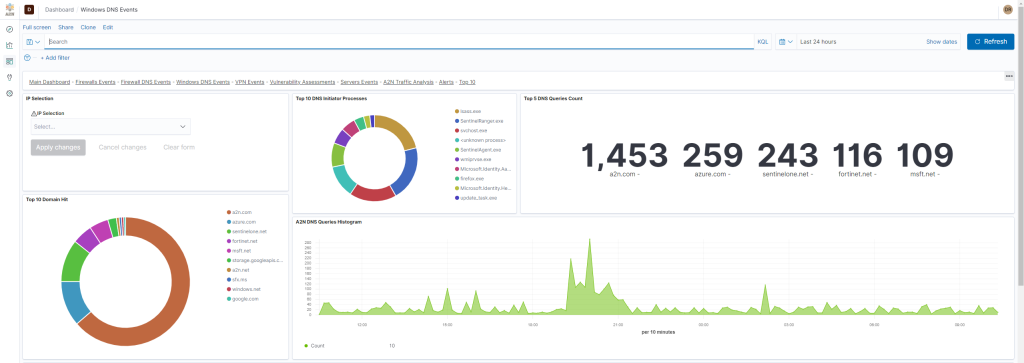
Our Single Pane of Glass Cloud Portal Offers Secure 7x24x365 Access to SIEM Data
SIEM360
Our basic SIEM package where you control the level of service based on the severity level of the asset being observed. SIEM360 includes: SOAR, Real-Time Threat Detection, Incident Analysis, Log Collection & Correlation, Incident Notification and Threat Modelling.
SIEM360+
Add Threat Hunting to SIEM360 and you have serious power to collect, compare and analyze threat data in real-time, to detect and stop attackers before they cause damage. Our collection of Indicators of Compromise (IOC) allows for in-depth SIEM Threat Hunting capability.
WatchToweR
A2N’s premier SIEM service combines Vulnerability Assessment results, Endpoint Detection & Response, Machine Learning and Behaviour Analytics with SIEM360PLUS. Pure SIEM power at Your control!
Dark Web Monitoring
Know What’s Out There Before It’s Too Late
Everyone Has Leaked Credentials. The Real Question Is: How Severe Is It?
Today’s visionary CISOs are looking outside the network to detect & remediate exposure that could leave them vulnerable. Flare’s SaaS platform automatically detects threats across the dark & clear web ranging from secrets leakage on public GitHub to stealer logs with corporate credentials being sold in private Telegram rooms.

A2N’s DarkWeb Sweep Service
DarkWeb Sweep is a mission-critical service that empowers organizations to continuously monitor their presence on the Dark Web. Our team provides around-the-clock surveillance—24/7/365—so you can stay protected without the need for constant oversight.
What we monitor:
- Leaked Assets & Intellectual Property
- Leaked Credentials
- Domains
- Third-party Vendor/Partner Lists
- Emails
- Executive and VIP Names
- IP & Subnet Ranges
Cybercriminals are continuously exchanging stolen credentials, sensitive data, and valuable company assets on the dark web. DarkWeb Sweep serves as your proactive shield—identifying what’s exposed, where it’s surfaced, and the potential impact on your business, so you can act before threats escalate.
Did You Know…
- The Dark Web makes up less than 1% of the total internet.
- The number of daily visitors to the Dark Web has risen to 3+ million.
- Around 60% of Dark Web sites are used for illicit activities.
- Over 15 billion leaked credentials are circulating on the Dark Web.
- These surged by 55.5%, with healthcare being the most targeted sector.
- Expected to reach $2.92 billion by 2032, growing at 21.8% CAGR.
- The U.S. and Germany account for 68% of global Tor network users.
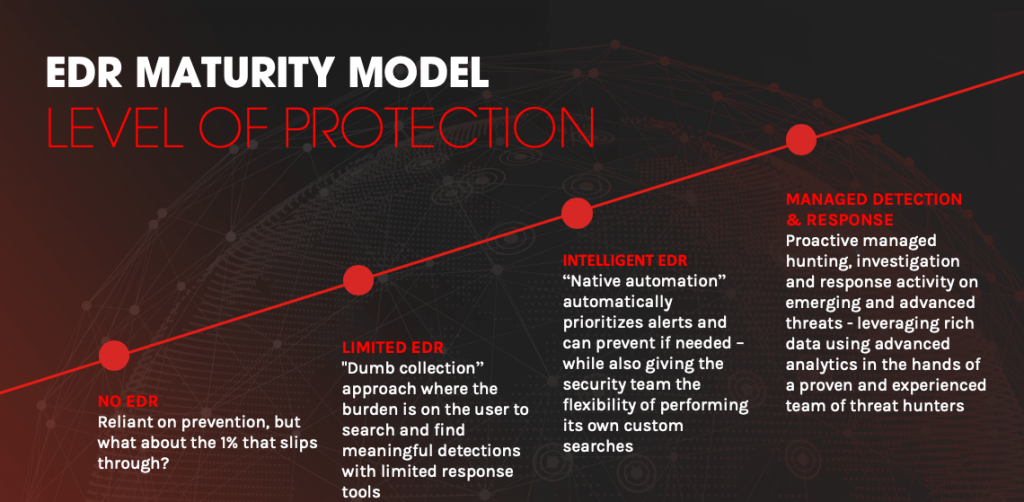
Managed Endpoint and EDR (MDR)
What is EDR and MDR?

Endpoint Detection and Response (EDR) and Managed EDR (MDR) are cornerstones of modern security posture, just as antivirus was 15 years ago. With advanced threats and the consequences of compromise high, the defense of the endpoint has been forced to evolve into an architecture that anticipates and preemptively protects from threats identified by known behavioral patterns.
EDR is considered the next generation Endpoint Protection because it uses a modern, sophisticated, and data-centered approach to preemptively detect malicious activity and respond to threats before endpoint compromise occurs. It can also be configured to automatically remediate a host if it’s compromised.
Managed EDR, or MDR, capitalizes on next generation endpoint protection technology by allowing our team of analysts, threat hunters, and operations experts to optimize and tune your EDR for maximum effectiveness and efficiency.
While EDR sounds like the superior defense, it comes at a cost — complexity. EDR solutions generate vast quantities of data which must be shipped off the endpoint. And if your organization is of any significant size, the data storage requirements can be overwhelming.
EDR is also configuration heavy. While endpoint protection is one install and a signature update from the vendor, EDR can involve configuration to ship log files to a central store for analysis. If that analysis happens in the cloud, there can be some delays in effectiveness.
Finally, EDR is great at determining threat detection with a high degree of confidence, but those findings are useless without a human analyst to verify them and define a course of action in response. If the data is large and “noisy,” the chances of quick response are low.
A2N’s Managed EDR provides you with a team of experts to tune your EDR solution to collect machine and user behavioral analytics for enhanced threat hunting opportunities.
Vulnerability Management
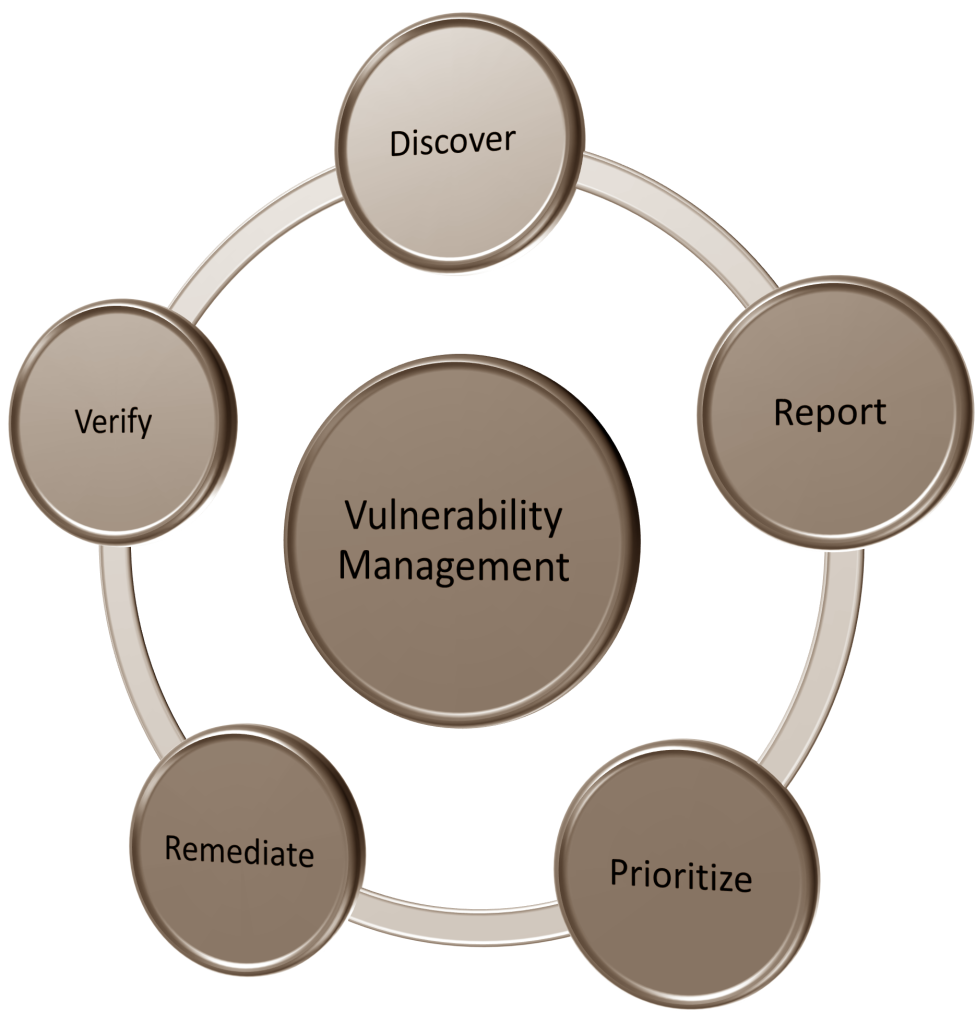
Conducting vulnerability assessment once a year or every quarter is no longer an accepted method of vulnerability management.
New vulnerabilities are being identified daily, and hackers are not waiting “until the end-of-quarter” to launch attacks against your networks; so why wait until it’s too late to discover your vulnerabilities?
Conducting vulnerability assessment more frequently (daily, weekly or monthly) will help you identify assets that require patches or upgrades, prioritize your assets and streamline your remediation strategy.
How Often Should Assessments be Conducted
Vulnerability assessments should be conducted frequently, but should vary depending on the type and number of assets being assessed. We recommend following a similar schedule and if you have a large number of assets then group them into manageable parts.
| Asset Type | Frequency |
|---|---|
| > External IP/System…………………………. | Daily |
| > Web Application…………………………….. | Weekly/Monthly |
| > Internal IP/System………………………….. | Daily/Weekly |
What Happens When Vulnerabilities Are Found
Vulnerability assessment results are constantly being monitored by our 7x24x365 SOC. When the service is first “spun-up” we baseline your vulnerabilities across the Enterprise. All vulnerabilities are identified and classified and we work closely with customers to help prioritize the asset and vulnerability for remediation. Tickets are used to closely track their progress until they are verified as remediated on follow-up assessments.
How Are VA Results Presented
A2N has a dedicated SIEM platform (SEIM360), and all vulnerability assessment results are stored within that platform.* The results are fully accessible from the A2N SIEM360 Portal, a “single pain of glass” portal that is secure and resilient. If you are already a SIEM360 customer then all of your SIEM logs and analytics will also be visible within your customer portal.
*Customers can also request hard backup.
We strongly recommend putting the SIEM Portal up on monitors within your SOC/NOC and on the desks of key cybersecurity staff & management.
From the SIEM360 Portal you can schedule a large number of default or customized reports to be generated on your schedule and to whomever you choose.
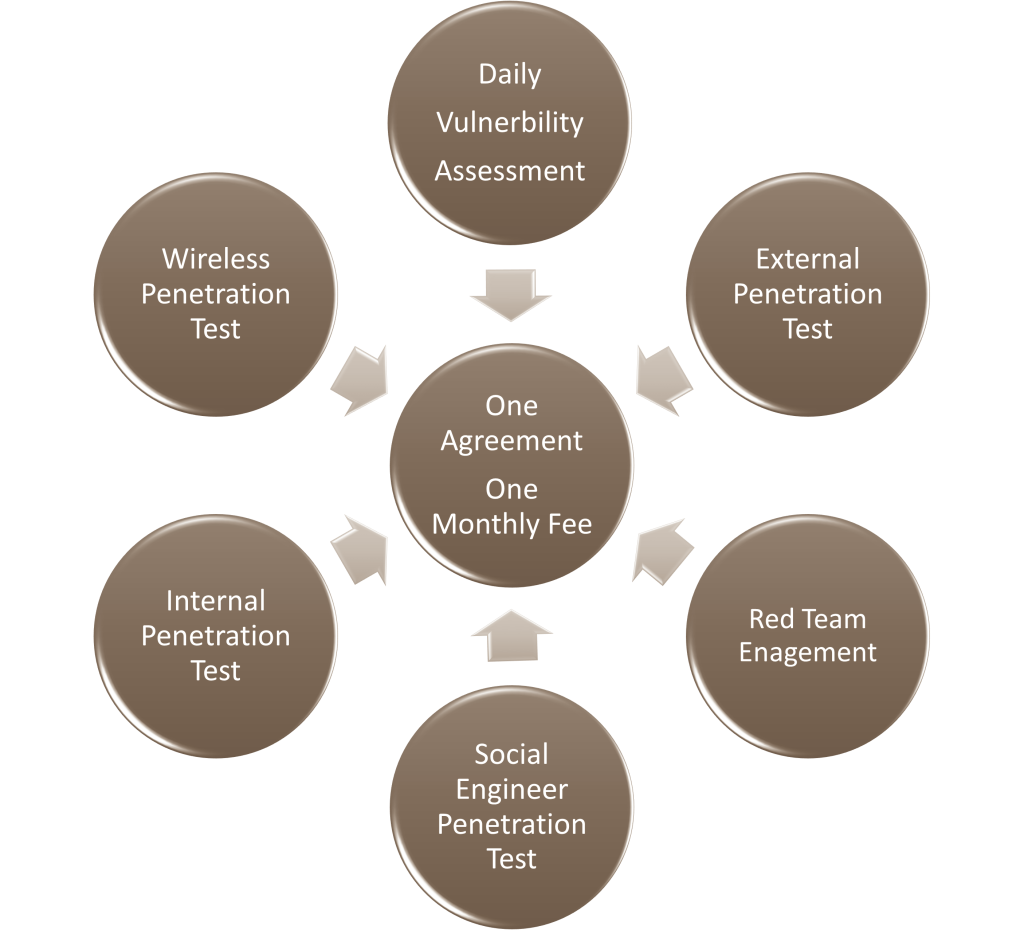
Complete Assessment Programs – Managed Assessments
While a Vulnerability Managed Service is effective, sometimes it can not stand on its own. What about penetration testing for external, internal, wireless, social engineering and Red Team engagements?
Customers want a single program to encompass all assessments; so we put together a complete Managed Assessment Service which includes all of your assessments within a single agreement and the convenience of a monthly fee.
What is a Red Team Engagement
A Red Team Engagement is an opportunity for IT & Cybersecurity Management to test and validate how effective their current monitoring and response capabilities are. During a penetration test we leave “bread crumbs” throughout the network starting with the complex and indistinct then slowly migrating to the very obvious. Your teams ability to spot intrusions and malicious activity within your network, using the tools and experience at their disposal, is how our Red Team will score and evaluate the response. A Red Team engagement is not to show how incapable your teams are but to unify and strengthen your capability by shoring up weaknesses found in tools, strategy and staff training.
Speak with your Account Executive about putting together a program for your unique assessment cybersecurity needs.
Managed WiFi
Your wireless network is a sophisticated architecture critical to your business and it requires effective and significant skill to manage and secure it effectively.
Many organizations have replaced “wire to the endpoint” with wireless technology to take advantage of the cost benefits, flexible in-office and site-to-site roaming capability and enhanced security features available within the technology; but business wireless can be very complex and difficult to troubleshoot without the proper knowledge, tools and skills.

Wireless solutions can include a varied use of technologies including Cloud based management, wireless access points, wireless controller, access switches, mobile & asset monitoring, and authentication & certificate services. The design & planning, deployment, implementation, integration, monitoring and on-going support & management of your wireless network can be a daunting task if you don’t have trained and dedicated staff. IT executives who find themselves in this situation are opting to offload the management of WiFi to 3rd party providers who specialize in the field.
Why Use A2N for WiFi Management?
A2N specialize in designing & implementing WiFi networks and WiFi security. We have a number of highly certified wireless experts on staff and we are recognized by our partners as having some of the most experienced and competent WiFi engineers in North America.




Managed Networks
Your wired network is the back-bone of your organization. Even if you have fully adopted a Cloud based or Hybrid strategy, and/or wireless to the endpoint, your corporate wired network is what bring all aspects of your connectivity together.
Your wired network is typically designed with a Core, Access & Distribution switches, depending on the size of your business, and each layer has a specific purpose. While many switched networks are designed with “old-school” Layer 2/3 methods, todays newer switched networks can have far more capabilities including; enhanced monitoring and SDN (Software Designed Network) functionality. However, it can also provide a lot more complexity and administrative conflicts.
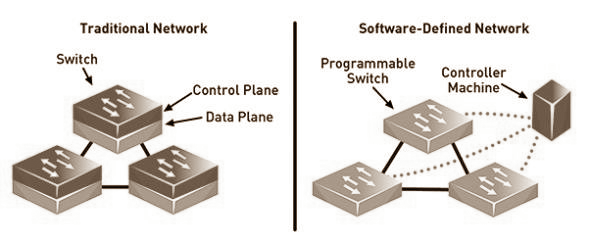
We recommend making use of today’s newer switching technology – but – don’t get caught Not knowing how to properly design & grow, configure, administer and manage the infrastructure. Utilizing a managed service to manage your networks could make sense if your resources are new or inexperienced, your budget for training or to hire experienced staff is limited, or you wish to off-load risk to a third party. A2N’s 7x24x365 managed service can help.
Managed Monitoring

MONITORING

ALERT VALIDATION

NOTIFICATION
Be Proactive With Infrastructure Monitoring and Alerts
COMPREHENSIVE MONITORING
Monitor your entire infrastructure – servers, storage, firewalls, VMs, web servers, application servers, database servers, operating systems, fan speed, CPU, disk I/O, memory usage, storage performance, and much more.
CONTEXTUAL ALERTS
We finely tune our NPM/APM to provide specific information on potential or actual problems to help validate issues speedup problem resolution.
NOTIFICATIONS
Alerts are processed by our SOC team, who can notify pre-identified contacts of potential issues. If you get a call at 3am, you know the concern is real.
PROACTIVE ACTION PLANS
Employ our team to take proactive measures to analyze performance and alerts, and take corrective actions.
Identify, Escalate and Resolve Issues Quickly
Managed Anti-Spam

Managed Anti-Spam is an enterprise threat prevention system that uses a sophisticated array of spam filters, reputation filters, anti-virus scanners and content analysis engines to prevent unsolicited mail from entering your network.
- Easy to Use
- Advanced Protection Methods
- Redundant Infrastructure
- Consistent & Stable Filtering
- AI Learning
- User or Administrative Quarantine Management
- Compatible with O365 and Hybrid Environments
- Cost Affordable
We strive to have the best Managed Anti-Spam Service in Canada that is affordable, 7x24x365 fully managed and supported, completely redundant environment and guaranteed to block 99.99% of all known bad spam based on reputation, spam filter, antivirus and AI learning based on user feedback.
Managed Phishing and Security Awareness

FACT: Most cybersecurity attacks are focused against a companies untrained user population in an effort to get them to click a button or a link or respond in some manner to the attacker. In an untrained business environment, our Social Engineering Penetration Tests are 100% successful.
Don’t Fall Victim to These Preventable Attacks
Security Awareness Training (SAT) when paired with automated Phishing Campaigns is a great way to continually test and validate your employees confidence in addressing attacks focused on your company or individual employees.

SAT is a fun and easy way to educate your employees, in an automated and professional method which is based on the learning styles and functions of your staff; from beginner to more advanced.
Some phishing attacks are very complex and very focused and they will get through; however, your companies ability to limit its exposures is multiplied with every successful denial. Phishing campaigns can be conducted as often as you wish and they can be as complex or obvious as needed depending on the knowledge & complexity of your staff. You can even group users so that the more advanced get more difficult phishing challenges.
Management can evaluate the results and make better decisions on the effectiveness of the training, if more training is required and the complexity of the training being offered. All of the information can be made private & confidential to meet all HR issues & concerns.
- New Employee Security Awareness Training (SAT)
- Bi-Annual SAT and Phishing Campaign Integration
- Monthly Randomized Employee Phishing Campaigns
- SAT Reviews and Employee Education Validation Sessions with Management