Professional Services & Solutions
We connect you with the right partners, products & solutions; then we plan, implement and support your investment.
We offer a wide range of cybersecurity services to help lead and support your organization though the complex world of Planning & Design, Growth Strategy, Governance, Assessments, Redundancy, Support, Monitoring & Management.
Implementations & Solutions
Cybersecurity is Complex – We Keep it Simple

Planning & Design
Product Implementation
Support Services
Helping you leverage your investment is one of our key objectives.

A2N’s expert sales staff will help you design a solution that is perfect for the unique needs of your business. We draw on years of expertise, experience and process refinement to help you get it done right!
- Expert Network & Security Design
- Partnering with the World’s Best Cybersecurity & Networking Manufacturers
- Trusted Sales and Procurement
- Experienced Planning
- Proof of Concept & Pre-Production Lab Testing
- Global Logistics and Deployment Strategy
- On-site and Remote Implementations
- Testing & Validation
- Knowledge Transfer & Training
- Documentation
- 7x24x365 Post-implementation Support and Managed Services
Our Solutions
- Firewalls & VPN
- Web Application Firewall (WAF)
- SD-WAN & Load Balancing
- SSL Visibility & Inspection
- Wired Networking
- Enterprise WiFi/Wireless
- Total Cloud Security | CASB | SASE
- SIEM & EUBA
- Detection & Response (EDR/MDR)
- Endpoint Security
- Reverse Proxy
- Anti-Spam & Anti-Virus
- Network & Application Monitoring
- Secure Collaboration & File Sharing
- Privilege Access Management
- Multi-Factor Authentication
- Zero-Trust Network Access
- Data Leakage Prevention (DLP)
- Intrusion Prevention Systems (IPS)
- Sandboxing Solutions
- Network Access Control (NAC)
- Way Finding “Blue-Dot” Beaconing
Contact your Account Executive or send an email to sales@a2n.net to get more information about our fantastic, end-to-end, implementation services.
Design & Strategy Consulting
Cybersecurity is complex maze of products, solutions and services. It’s important to build security into every aspect of a businesses corporate asset and network protection strategy but at what cost? How are you going to manage and maintain it? How do you know if your strategy is the right one for your business?
Asking experts for help makes sense; and it can save you a lot of headaches, maybe even your job, when you seek & select the right cybersecurity partner.

A2N’s cybersecurity consultants take a holistic approach to protecting your assets:
- Budget
- Business Sector (Finance | Education | Government | Etc..)
- Business Compliance & Mandated Objectives
- Security Risk & Vulnerability Rating
- Legal Requirements
- Future Proof & Growth Needs
- Leveraging Existing Cybersecurity Capital Assets
- Administrative Strengths & Weaknesses
- Employee Training
- Managed Service Acceptance
- Best-Value or Best-Breed Products/Solutions
- Technology & Business Disruptions & Paradigm Shifts
- Existing Cybersecurity Policy Directives
We ask a lot of questions but we do just as much listening.
Tell us where you need to go and we’ll help you get there.
Cloud Security
Enterprises seek out Cloud solutions when their business needs exceed the capabilities of on-premises environments. But, migrating to the cloud can manifest new cybersecurity challenges. Maintaining visibility, control, auditability and security as you move to hybrid cloud environments is a challenge. During your cloud transformation journey, at each critical stage, you need cybersecurity management to stay the encroachment of advanced threats.
A2N’s Strategic Cloud Approach
- Consider All Sections of Your Business
- Create a Cloud Security Mapping
- Security Build & Manage for the Cloud
- CASB for Corporate Applications
- Enhance Cloud Security Skills & Training
- Centralized Visibility Across All-Cloud Platforms
Cloud Migration can be a Smart Move. Securing Your Cloud IS the Smart Move.
Cybersecurity Assessments

There are many types of cybersecurity assessments, each with the goal of identifying gaps within the existing cybersecurity architecture, overall security posture, risk, governance & compliance, support & monitoring strategies and resources.
Identifying vulnerabilities, gaps, weaknesses (and strengths) within your business is the first step to understanding how to properly plan & design for the future.
A2N’s Cybersecurity Assessment Services:
Architecture & Governance
- Network & Cybersecurity Architecture
- Complete GAP Analysis
- Threat Risk Assessment (TRA)
- Wireless Architecture Performance
- Cybersecurity Policy Review
- Incident Response (IRP) Review
- NIST Compliance
- Staff Security Awareness
- Firewall Audit
Systems & Applications
- Vulnerability Assessments
- Penetration Testing
- Web Application Assessments
- Wireless Penetration Testing
- Social Engineering
- PCI Vulnerability & Penetration *
*A2N is not a certified QSA or ASV, however, we can be used for most of your PCI assessing needs.
Check out A2N’s Managed Vulnerability Assessment and WatchTower Programs
HOT TOPIC – Cybersecurity GAP Assessment
A2N’s Gap Assessment is our hands-on method of diving into your cybersecurity and network architecture. Through white boarding sessions, face-to-face consultations and many questions with your team we can quickly ascertain if your security posture meets your business objectives, or, if you are vulnerable by design. We make simple and straight-forward recommendations for gap mitigation which make sense for your business.
Governance, Risk, Compliance (GRC)

You must fully understand where risk may cause impacts, and how to properly leverage risk management. Threats and vulnerabilities are a great place to start when defining risk management. Learning how to qualify and quantify your risk against asset value will help you make informed decisions on future direction and budget need.
Governance, risk and compliance (GRC) fall in line together. Risk is understanding the uncertainty surrounding your assets; while compliance focuses on the policies and regulations you either adopt or are compelled to follow. Governance is key when applying processes and practices to the entire operation of compliance; but how deep should take GRC within your company?
7x24x365 Monitoring Services
As your business grows, so does your expectation of performance and resiliency, but how do you adequately monitor and support your networks and applications when experienced practitioners are difficult to find.
Can you afford to have downtime? When things go wrong, can your on-premise team get things working again quickly, efficiently and securely? A knowledgeable partner can get your network working again in minutes instead of hours or days. Only you can make the call on what your companies downtime is worth.
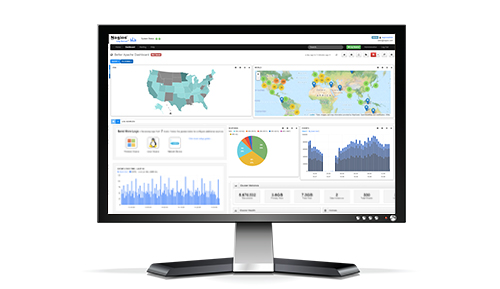
With A2N, you’ll always have eyes on your network. When something goes wrong, you can expect us to follow up with a phone call from an actual 7x24x365 SOC engineer located in Ontario, Canada (not overseas).
It’s relatively simple to ping an IP or collect SNMP polls, but, it takes skill and experience to create custom pollers and processes to know if your applications and networks are actually working as intended.
Application Monitoring
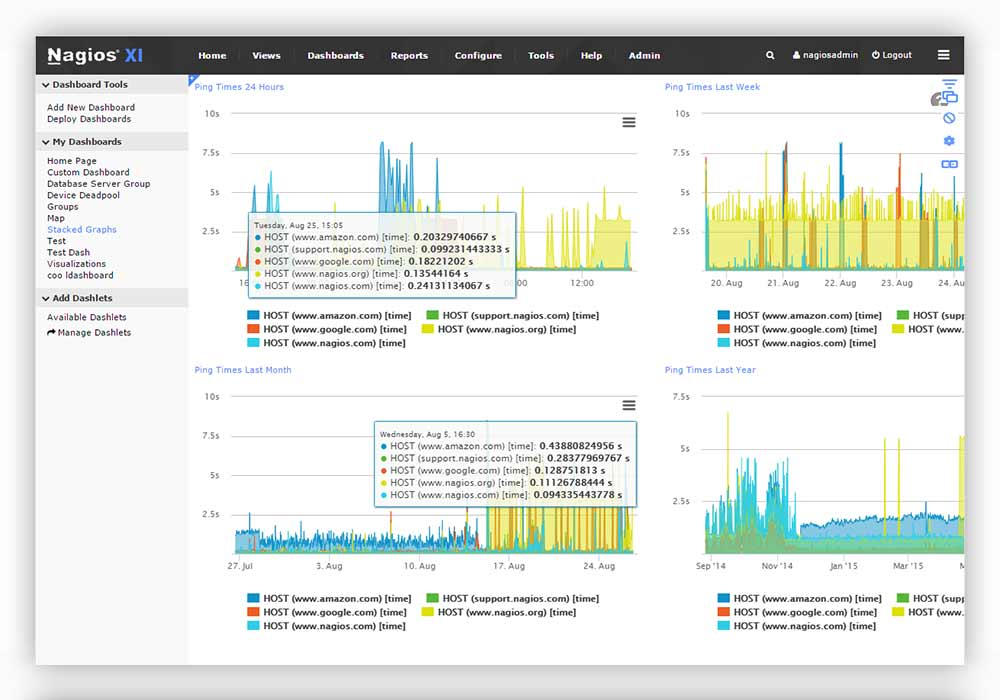
It’s relatively simple to ping an IP or collect SNMP polls, but, it takes skill and experience to create custom pollers and processes to know if your applications and networks are actually working as intended.
A2N provides complete monitoring of applications and application state – including Windows applications, Linux applications, UNIX applications, and Web applications.
Benefits
- Increased server, services, and application availability
- Fast detection of network outages and protocol failures
- Fast detection of failed services, processes and batch jobs
BANDWIDTH MONITORING
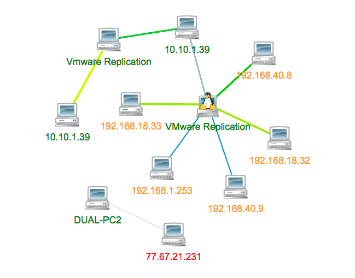
Visibility is the key to quickly and accurately identifying the root cause of network issues. We offer affordable, appliance-based and software solutions that are trusted globally by large and small organizations from an array of industries including: military, financial, insurance and information technology firms.
We will continuously scan, monitor, and report any activity throughout your network offering you with complete insight. Our solutions track bandwidth consumption, network latency, disk usage, event logs, device status and battery backup states –just to mention the obvious!
ENVIRONMENTAL MONITORING
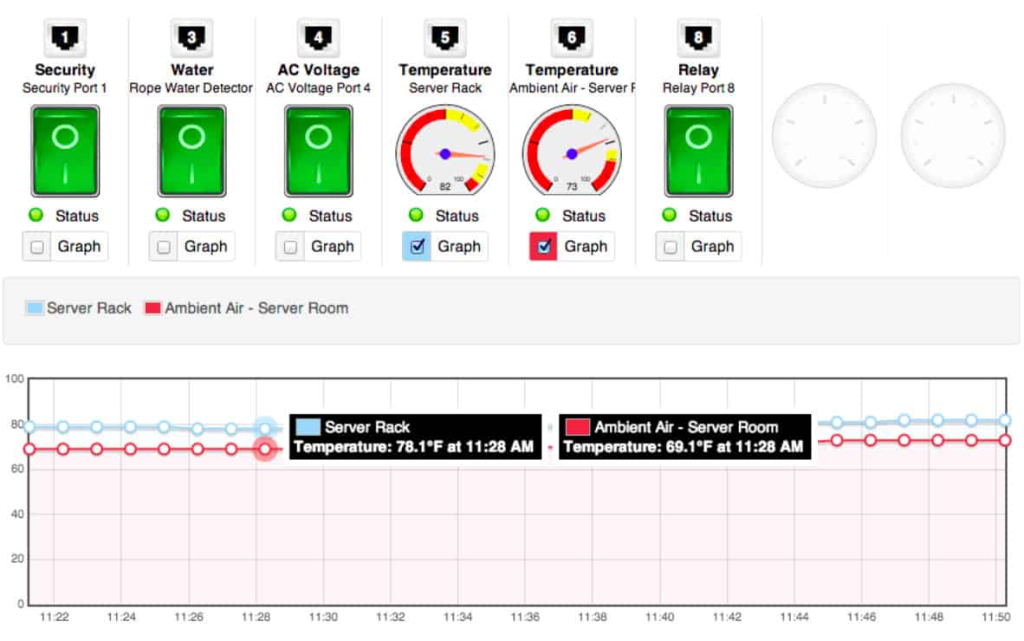
Do you have concerns with environmental conditions, such as: temperature, water and airflow? Allow A2N to monitor these conditions in your server rooms, data centers, or building mechanical areas.
- Cameras – Pan and Tilt
- Temperature Sensors
- Humidity Sensors
- Liquid Detection Sensors
- Voltage Sensors
- Airflow Sensors
- Motion Sensors
- Smoke Detectors
- Doors & Security Sensors
- Dry Contact Sensors
7x24x365 Support Services
For the times you want the assurance and peace of mind of having a local expert resource available to answer questions or remotely fix a problem. Our Security Operations Center (SOC) is uniquely qualified to do just that. Because we already understand your environment and your implemented solutions we don’t force you to go through a Level 1 to Level 3 support queue – you go to the “front of the line” and speak directly with our experts.

We offer:
- 8×5 & 7x24x365 Email, Telephone and Web Portal Support
- Remote “Break Fix”
- RMA Intervention
- Manufacturer Advocate
- First Call Support
ANNUAL MAINTENANCE
Our on-site and remote maintenance support is one of the hottest service we offer. If your IT department is concerned about conducting upgrades and patch modifications to production systems then a maintenance program is right for you.

Maintenance packages include:
- Two annual site visits (remote/onsite as permitted) to upgrade and patch your solutions
- Offsite storage of your OS & policy configuration
- Passwords backup (just in case you forget)
- A basic policy review with verbal recommendations
- Q&A: We will answer any solution related questions
Combined with our support package your business will be well supported.
Outsourcing & Staff Augmentation
The skills gap is widening very quickly between technology, staff training, experience and hiring feasibility. Seasoned cybersecurity staff are very difficult to find.
If you have:
- Lost your skilled cybersecurity resource
- Can not afford to send your limited resources on training
- An immediate need for an experienced cybersecurity professional
- Have projects building up or going stagnant on the shelf

Then using a skilled resource, outsourced from A2N, may be your answer. We can outsource for extended periods of time and at any skill level:
- Junior
- Intermediate
- Senior
- Project Management
If outsourcing doesn’t appeal to your organization then perhaps our managed services would be a more appropriate fit. Talk with your account executive and make the right decisions for your business.
Phishing Campaigns

A phishing campaign is an assessment run by internal IT staff or a 3rd party which tests and rates the skills of an organizations user population to identify spam and phishing emails. The phishing campaign is normally performed without notification to get more accurate results. If a user responds or clicks on an inappropriate link then that information is stored for management and cybersecurity staff to review and evaluate.
Over a period of time, a complete understanding of staff security awareness is presented and can be used to identify staff or groups for additional education or training. The goal is not to single out or discipline staff but to educate and enhance the organizations security posture.
Phishing campaigns are always more successful when paired with an appropriate cybersecurity awareness training strategy. Often, these two concepts can be bundled together within a single solution.
Security Awareness Training
Security awareness training is critical because hackers don’t take breaks and cyber threats abound and are continually changing. Your employees are the common thread for some of the most significant threats to your organization. Hackers know uneducated people can be easily compromised and make a very soft attack vector – making their exploits very successful.
A well-trained and vigilant employee is the best means of securing your business.

We tend to expect a little too much from our employees when it comes to understanding the risks associated with their IT and online habits. We tell them, “DON’T click on this” and “DON’T do that” without really informing them why this is necessary. Over time they get desensitized to cybersecurity and just expect the IT department to make it all right. More often than not, there is an acute lack of understanding by employees of what their actions might do and how they can place an entire organization in jeopardy.
Without a doubt, users/employees are the least secure aspect of an organization’s cybersecurity strategy. While attempts can be made to secure the enterprise a user can unwittingly circumvent that security by clicking on a destructive link or being tricked into sharing the wrong information.
Rather than a one-time event, security awareness training is most useful when approached as a critical ongoing practice in the context of a bigger security awareness program. The training and the program are integral to building a culture of security in today’s digitally dependent organizations.
Security Awareness Training has been proven to:
- Reduce overall threats and risk to the enterprise
- Increase an employee’s benefit to an organization
- Encourage employee growth and self-esteem
- Increase company and employee morale
- Promote positive business and work ethics
- Improve networking and the sharing of ideas
- Provide a higher quality of education and learning
Authorized Training Center
A well-trained and vigilant employee is the best means of securing your business.

Instructor Led Training

Virtual Instructor Led Training

“On-Site” Training

A2N was the first Fortinet Authorized Training Centre (ATC) in Canada. Certified as an ATC in 2018, we have trained more engineers in Canada than any other facility. All of our instructors are implementation engineers with years of experience and certifications.
A2N is the ONLY Checkpoint Implementer in Canada with ATC Status. As one of Canada’s top Check Point Authorized Training Centre’s you will receive world-class coaching from seasoned and certified instructors with real-world experience.


As a private VUE Testing Center, you can take your certification test following your course. A2N will get you ready – the rest is up to You!
Contact your Account Executive now for pricing and information. Or, contact sales@a2n.net.
A2N siteSECURE
SITESECURE IS NOT LIKE OTHER TRUSTMARK PROGRAMS.
WE DON’T SELL SSL CERTIFICATES AND CLAIM SITES ARE SECURE.
WE CONDUCT VULNERABILITY AND PENETRATION TESTING AGAINST WEB SITES AND WEB APPLICATIONS.
WE PROVE THAT EACH SITE IS 100% FREE OF VULNERABILITIES AND CONTINUALLY ASSESSED TO ENSURE IT STAYS THAT WAY.

Unlike other secure site offerings, we don’t focus only on certificates, which is an important but relative small component of web application security. Our service focuses on ensuring all vulnerabilities and penetrable vectors are mitigated or remediated. Your web site will be thoroughly tested by A2N’s dedicated assessment team and when it is free of vulnerabilities we issue you a certificate and your siteSECURE trustmark designation – your web application is 100% free of vulnerabilities and exploits.
The A2N SECURE service is a paid service for website owners that examines their websites for potential vulnerabilities on a daily basis, and, if no issues are found, enables the site to display the A2N siteSECURE trustmark. The A2N web site contains additional specific terms governing the A2N siteSECURE service at this link.
siteSECURE Certification Program
Companies wishing to display the siteSECURE certification within their business must meet the following requirements:
- A full penetration test conducted every 6 months by A2N
- A mandatory retesting for every major code revision or platform change conducted by A2N
- Proof that 100% of vulnerabilities have been mitigated
- Bi-Annual Fees
siteSECURE Trustmark Program
Companies wishing to display the siteSECURE trustmark within their business and on their website must meet the following requirements:

- A full penetration test conducted every 6 months by A2N
- A mandatory retesting for every major code revision or platform change conducted by A2N
- Weekly vulnerability assessing conducted by A2N
- Proof that 100% of vulnerabilities have been mitigated
- Bi-Annual Fees
Please refer to the complete list of terms and services for more details surrounding the service.

If the A2N siteSECURE trustmark is visible then you can feel assured that the site is safe to visit.*
THIS SITE IS SAFE TO CONDUCT BUSINESS!
If you have any questions regarding this trustmark please contact A2N’s siteSECURE Assessment Team.
Our Professional Services
- Overview
- Implementations & Solutions
- Design & Strategy Consulting
- Cloud Security
- Cybersecurity Assessments
- Governance, Risk & Compliance
- 7x24x365 Monitoring Services
- 7x24x265 Support Services
- Outsourcing & Staff Augmentation
- Phishing Campaigns
- Security Awareness Training
- Authorized Training Center
- Web Site Certification (A2N siteSecure)